What is Mimblewimble? The Complete Beginner’s Guide
The phrase “Mimblewimble” has been trending in the crypto community in the last few weeks. If you are a Harry Potter fan, you have probably come across this word. Mimblewimble is the tongue-tying curse that binds the target’s tongue to keep them from talking about a specific topic or subject.
Mimblewimble is a famous phrase in the crypto world as it is the name of a newly trending protocol. The Mimblewimble protocol relies on strong cryptographic primitives. Therefore, it provides an excellent framework for a blockchain that has good scalability, privacy, and fungibility.
Today, we are going to explore this innovative protocol. We’ll talk about what it is, how it works, its main applications, and the top players who’ve already implemented it.
What is Mimblewimble?
Tested for decades, Mimblewimble uses elliptic-curve cryptography that requires smaller keys than other cryptography types. In a network that is using the Mimblewimble protocol, there are no addresses on the blockchain, and the network’s data storage is highly efficient.
Mimblewimble needs about 10% of the data storage requirements of the Bitcoin network. This makes Mimblewimble highly scalable for storing the blockchain, significantly faster, and less centralized. Furthermore, the nature of the protocol allows for private transactions that are highly anonymous (more about this later).
The birth of Mimblewimble
Rejoice, Harry Potter fans! Another reference is coming from the movie fan world. The Mimblewimble Whitepaper was first published on July 2016 in the Bitcoin research channel under the anonymous author name of Tom Elvis Judisor – the French name for Voldemort.
Soon after the whitepaper was published – at the end of 2016 -, another anonymous user with the pseudo name “Ignotus Peverell” (the original owner of the invisibility cloak from the Harry Potter universe) started a Github project with the application of the Mimblewimble protocol. This project is called Grin, which released its mainnet on January 15, 2019. There’s also another implementation of Mimblewimble, Beam, that has been already released. We will talk about Grin and Beam later in this article.
How does it work?
To understand Mimblewimble, we’ll first have to explain Bitcoin’s UTXO (unspent transaction output) model. If you are paying with fiat – using the Alice and Bob example below. If Alice gives Bob 1 USD, it will look like this:
Alice: -1 USD
Bob: +1 USD
It’s not the same in the Bitcoin network. BTC transactions are made of several inputs and outputs that go from the sender to the receiver. If you’ve checked your recent Bitcoin transactions, You’ve probably seen both inputs and outputs on the website of the blockchain explorer.
So, Bitcoin works as follows. Alice wants to send 1 BTC to Bob. Instead of just deducting one Bitcoin from Alice’s wallet, the network bundles up multiple inputs from previous BTC transactions that were sent to Alice to equalize the one coin Alice sends to Bob. Therefore, this Bitcoin transaction could look like this:
Alice: – (0.1+0.25+0.35+0.3) BTC where A+B+C+D are all inputs that have been bulked up
Bob: + 1 BTC
In this example, Alice’s 1 BTC was made up of four inputs. But there are cases in the Bitcoin network when one transaction has hundreds of inputs. Furthermore, if the sum of the inputs is greater than the transaction amount, the transfer will create an additional output. This way, the first output will include the exact amount that will go to the receiver, and the rest will be returned to the sender. As every transaction has to be individually signed by wallet software, the network has to process tons of data. This process is highly inefficient.
Confidential Transactions
This is the point where Mimblewimble comes into the picture. As mentioned before, the protocol proposes a much more efficient system, eliminating inputs and outputs. The UTXO model is replaced by one multisignature for all inputs and outputs which are called Confidential Transactions. If Alice wants to send Bob a coin, both Alice and Bob create a multisignature key that is used to verify the transaction.
Confidential Transactions use the Pedersen Commitment scheme; there are no addresses. Instead, the parties share a “blinding factor”. The blinding factor encrypts the inputs and outputs of the transaction along with both parties’ public and private keys. This blinding factor is shared as a secret between the two parties who were engaged in the transaction. Due to the blinding factor replacing addresses, only the two parties know that they were involved in a transaction. This keeps the privacy of the network at a high level.
The Pedersen Commitment scheme works as follows. Full nodes deduct the encrypted amounts from both the inputs and outputs, creating a balanced equation that proves that no coins were produced out of thin air. And during the whole process, the node does not know the actual amount of the transaction.
The only verification needed in the Mimblewimble protocol is to check that no new coins were created and that the parties taking part in the transaction have ownership of their keys. Both verification processes use the blinding factor to keep the transaction value private. Let us show you the process:
- 5+5=10 — 5+5-10=0
The above simple example shows that no new coins were created – indicating that the net balance is zero.
- 5(10)+5(10)=10(10)
A secret number (10) – the blinding factor – is added to this calculation, which is multiplied by all variables. This is used to obscure the original values.
- 50+50=100
In this equation, both the blinding factor – which was 10 in the second equation – and the values remain private while still allowing others to verify that no new coins were created in the transaction.
In Mimblewimble, the blinding factor is a combination of the public and private keys. This way, in addition to proving that no new coins were created, the parties can prove that they are the owners of their keys.
The parties of the transaction are both given a multisignature header at the end of the transaction. This multisig header consists of all the inputs and outputs of the transactions that are merged.
Cut-Through
The important feature of Mimblewimble regarding scalability is “Cut Through”. A single block consists of hundreds of transactions as well as plenty of information that needs to be stored on the blockchain. However, these blocks can be compressed with Mimblewimble’s Cut Through feature as a large part of the info can be removed from the blocks without risking the security of the blockchain.
Here’s a simple example:
- Alice sends 1 BTC to Bob.
- Bob sends 1 BTC to Charles.
In this case, a typical block has two UTXOs. The first UTXO will hold the input for that 1 BTC which reflects how it got to Alice. The output for the first UTXO is the result of the transaction, which verifies that the Bitcoin is now owned by Bob. The second UTXO consists of the output of the first UTXO – which is now the input of the second UTXO – and the output of the second transaction to Charles.
This means that Mimblewimble eliminates the output of the first transaction and the input of the second transaction. So, we’ll only have one input and one output – that verifies how Alice got this 1 Bitcoin and how Charles received their 1 BTC -, instead of having two of each.
This compresses the size of the blockchain, making Mimblewimble much lighter regarding the data storage.
Grin and Beam vs. Zcash and Monero
As of January 16, 2019, two ASIC-resistant coins have implemented the Mimblewimble protocol. Grin has been in development since late 2016. The developers launched the mainnet on January 15, 2019. On the flip side, Beam already has its working mainnet.
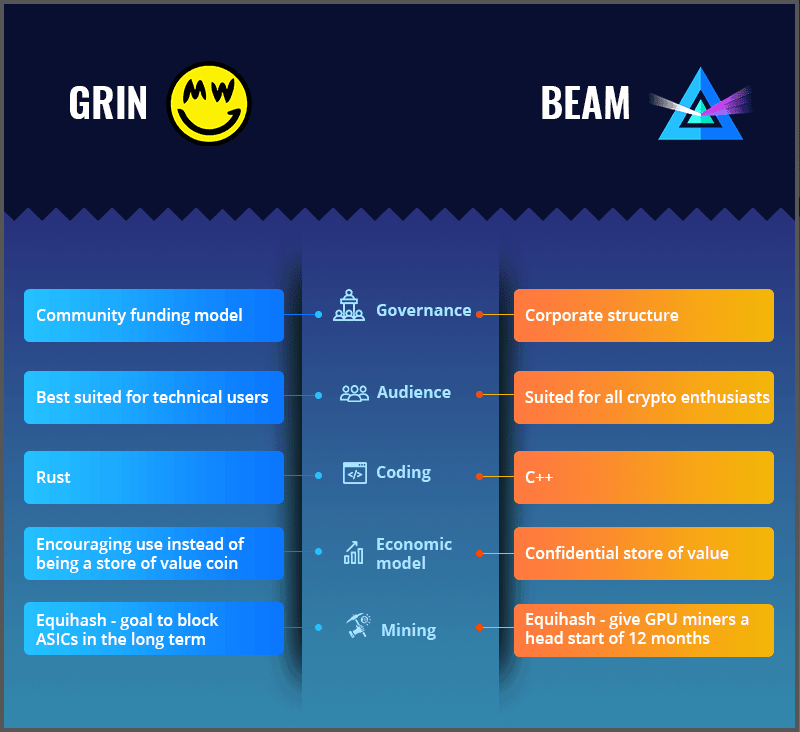
hile the two coins use the same protocol – Mimblewimble -, they have grand differences. Beam has a corporate structure; the company has collected VC funding and hired a development team, which allowed them to win the development time race against Grin. Beam’s Foundation relies on the part of the block rewards it gets to support the development of the network. On the flip side, Grin has governance that is similar to the cyberpunk ideology that empowers a community-driven decentralization. There’s no ICO, token pre-mine, and the developers are volunteers.
The two coins differ in usability and audiences too. Beam has a more professional stance in regards to the cryptocurrency’s use-cases; the team has built a simple wallet interface that is aimed at being user-friendly, with implementations for different operating systems, including Mac, Windows, and Linux. This way, the ordinary crypto enthusiast can access the Beam blockchain. On the other hand, Grin is not so user-friendly, because the coin only offers a command-line wallet which is accessible by more technical users.
Grin is using the Rust programming language, while Beam was coded in C++. This is not a significant difference between the two cryptos. The same can’t be said of the economic models. While Beam’s goal is to be used as an anonymous store of value, Grin developers argue that Grin should be used as a “currency”, instead of a store of value. Grin supporters don’t want to “unfairly reward” early adopters, they want to increase adoption instead.
In regards to mining, both cryptocurrencies use the modified versions of the Equihash algorithm. While both coins are ASIC-resistant, their goals are different. Grin seeks to fully implement their version of Equihash (Cuckoo Cycle) in two years, while Beam wants to use an ASIC-resistant mining algorithm for 12 months, to give GPU miners a head start.
Now, let’s see how these two coins compare to the three most popular privacy coins: Zcash, Monero, and Dash. According to critics, Zcash’s ring signatures and zk-SNARK’s are too computationally intensive, which results in slow and expensive transactions (compared to Beam and Grin).
Monero uses “mixins” to make transactions private. However, according to an analyst, 64% of all inputs do not contain mixins, so those transactions are not private. Other researchers argue that about 80% of Monero transactions could be traced.
And finally, Dash is considered the most centralized of all privacy coins, which makes the cryptocurrency less private. Though Dash has advantages in regards to scalability, people who want to remain entirely anonymous will be discouraged from using the coin because of its increased centralization.
Conclusion
While Monero and Zcash are popular privacy coins that are widely used in the crypto community, their networks can be improved with new technology, such as Mimblewimble.
If the creators of the coins’ (which can include non-anonymous currencies, such as Bitcoin) thoroughly analyze and follow the development of Grin and Beam, cryptocurrencies can become more private and anonymous again.
The post What is Mimblewimble? The Complete Beginner’s Guide appeared first on CryptoPotato.